Department of Computer Science
Research Posters
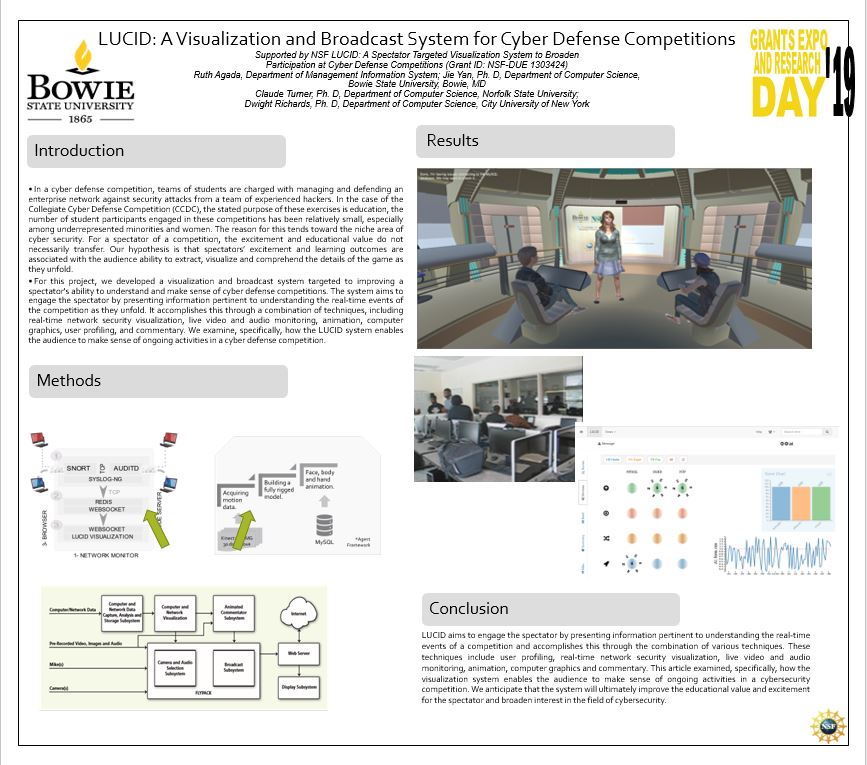 LUCID: A Visualization and Broadcast System for Cyber Defense Competitions
LUCID: A Visualization and Broadcast System for Cyber Defense Competitions
- Ruth Agada, Department of Management Information Systems
- Jie Yan, Ph. D, Department of Computer Science
In a cyber defense competition, teams of students are charged with managing and defending an enterprise network against security attacks from a team of experienced hackers. In the case of the Collegiate Cyber Defense Competition (CCDC), the stated purpose of these exercises is education, the number of student participants engaged in these competitions has been relatively small, especially among underrepresented minorities and women. The reason for this tends toward the niche area of cyber security. For a spectator of a competition, the excitement and educational value do not necessarily transfer. Our hypothesis is that spectators’ excitement and learning outcomes are associated with the audience ability to extract, visualize and comprehend the details of the game as they unfold.
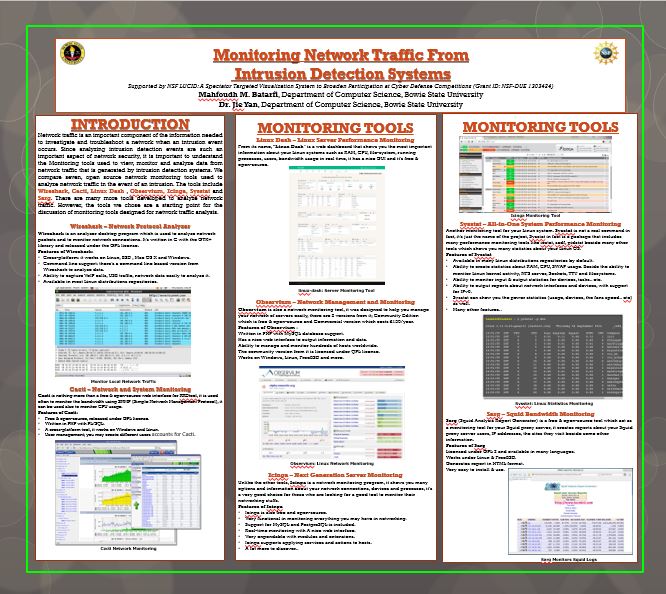 Monitoring Network Traffic From Intrusion Detection Systems
Monitoring Network Traffic From Intrusion Detection Systems
- Mahfoudh M. Batarfi, Department of Computer Science
- Dr. Jie Yan, Department of Computer Science/academics/colleges/college-of-arts-and-sciences/departments/computer-science/research/labs/monitoring-intrusion-poster.pdf
Network traffic is an important component of the information needed to investigate and troubleshoot a network when an intrusion event occurs. Since analyzing intrusion detection events are such an important aspect of network security, it is important to understand the Monitoring tools used to view, monitor and analyze data from network traffic that is generated by intrusion detection systems. We compare seven, open source network monitoring tools used to analyze network traffic in the event of an intrusion. The tools include Wireshark, Cacti, Linux Dash , Observium, Icinga, Sysstat and Sarg. There are many more tools developed to analyze network traffic. However, the tools we chose are a starting point for the discussion of monitoring tools designed for network traffic analysis.
A Cryptographic Simulator for Enhancing Undergraduates’ Learning Experience in Cybersecurity Education
- Ayodeji, Ogundiran, Department of Computer Science
- Jie Yan, Department of Computer Science
- Chaobin Liu, Department of Mathematics
Cryptography is one of the most important tools for building secure systems. It can be used to achieve several goals of information security. Through the proper use of cryptography, one can ensure the confidentiality of data, protect data from unauthorized modification, and authenticate the source of data. In cyber security, cryptography is a very important and necessary tool that covers encryption and decryption algorithms, cryptographic protocols, and cryptanalysis. Due to the importance of cryptography, National Centers of Academic Excellence (CAE) guidelines have included cryptography as the core knowledge for information assurance and cybersecurity education accreditation. These guidelines have been incorporated into the syllabi and curriculum of colleges offering computer science and information security as majors. However, there are still a few major barriers for students at HBCU institutions to comprehend the core concepts of the cryptography.
 Multi Sensor Performance Driven Data Fusion for Sign Language Synthesis
Multi Sensor Performance Driven Data Fusion for Sign Language Synthesis
- Tunde Akinlaja, Department of Computer Science
- Ruth Agada, Department of Management Information System
- Jie Yan, Ph. D, Department of Computer Science
Sign Language is a visual language that is used by hearing impaired peoples for communication. Sign language is composed of three features, namely manual signs, non-manual signs, and finger-spelling. Manual signs are the gestures that are represented by hand shapes, motions, and positions, whereas non-manual signs contain facial expression or body postures. They add syntactical information to the gestures that can be the part of a sign or modify the meaning of a manual sign. In finger-spelling gestures, different words are spelt out in local verbal language using fingers during communication Hence, Sign Language Recognition (SLR) systems aim to provide a robust and reliable interface capable of handling the complex requirement of the language and through which one can get feedback while interacting with a signer.